The following page may contain information related to upcoming products, features and functionality. It is important to note that the information presented is for informational purposes only, so please do not rely on the information for purchasing or planning purposes. Just like with all projects, the items mentioned on the page are subject to change or delay, and the development, release, and timing of any products, features or functionality remain at the sole discretion of GitLab Inc.
Security visibility from development to operations to minimize risk
GitLab provides the single application organizations need to find, triage, and fix vulnerabilities, from development to production. This empowers organizations to apply repeatable, defensible processes that automate security and compliance policies that proactively reduce overall security risk.
The Sec section focuses on providing security and compliance visibility across the entire software development lifecycle. We accomplish this by:
GitLab is uniquely positioned to fully support DevSecOps by providing a single application for the entire software development lifecycle. This includes both shifting Application Security Testing (AST) left as well as providing visibility and control over security and compliance findings, from first line of code to production.
GitLab's single application maps directly to the DevSecOps lifecycle. GitLab's AST stage focuses on pinpointing vulnerabilities and weaknesses, from development to production, while the Security Risk Management (SRM) stage provides visibility and control over the security findings AST detects. Software Supply Chain Security (SSCS) makes GitLab a verifiably secure foundation for software delivery. Together, GitLab supports all teams involved in delivering secure applications:
Remediating security vulnerabilities earlier reduces risk and makes remediation cheaper.
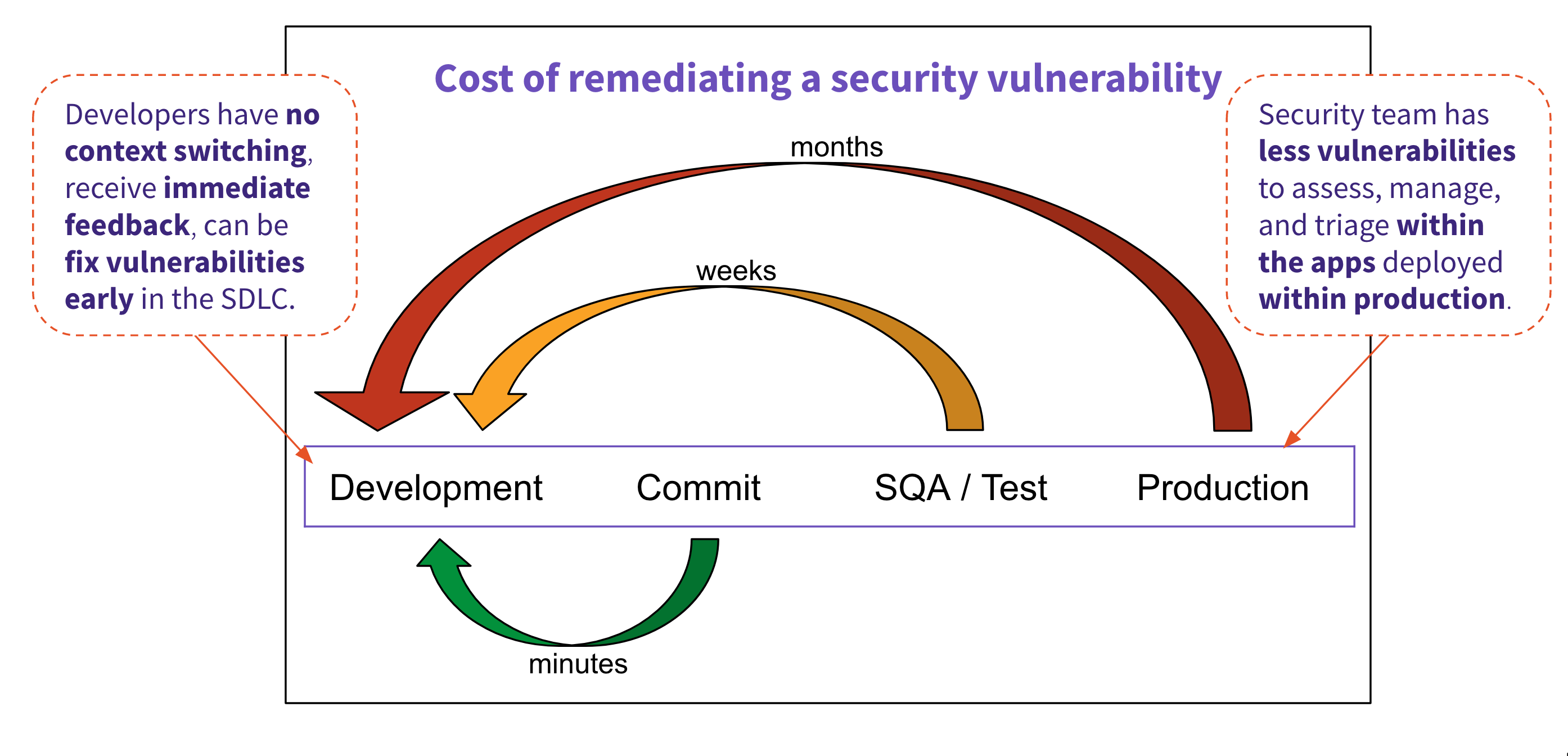
When security vulnerabilities are identified at the time of code commit, developers can understand how their newly introduced code has led to this new issue. This gives the developer a cause-and-effect enabling quicker resolution while not having the time hit of context switching. This is not true as security scanning is performed later in the software development lifecycle. New vulnerabilities may not be identified until weeks or months after they were added to the application while under development.
Time is not the only savings when shifting security left.
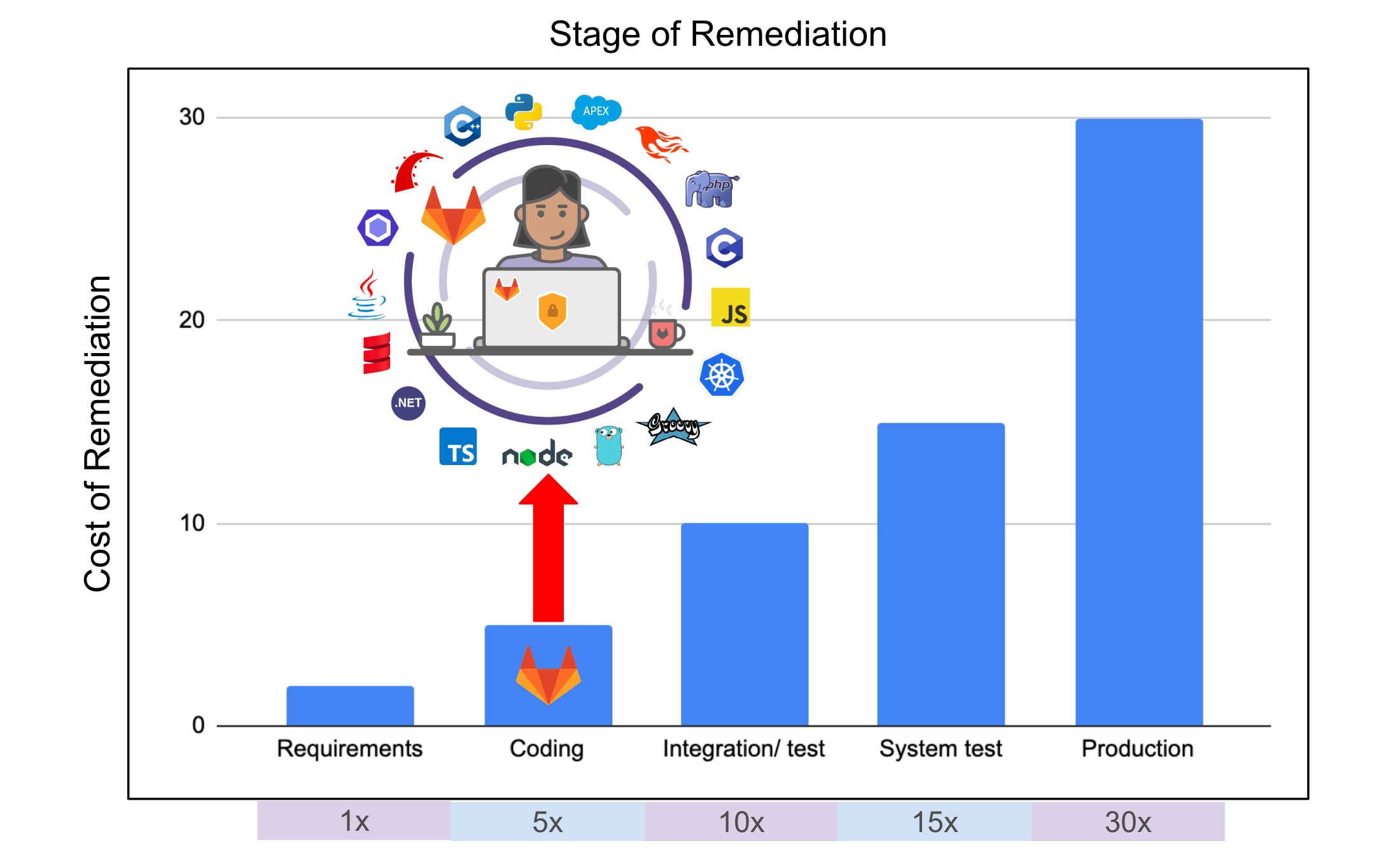
In “The Economic Impacts of Inadequate Infrastructure for Software Testing”, NIST estimated the cost of remediating software bugs at $59.5 billion/year. This is compounded when taking in the average time to remediate software bugs. In “Software Development Price Guide & Hourly Rate Comparison”, FullStack Labs estimates the average cost of a software developer at $300/hour. The following table outlines the cost to remediate software bugs at different stages of the software development lifecycle:
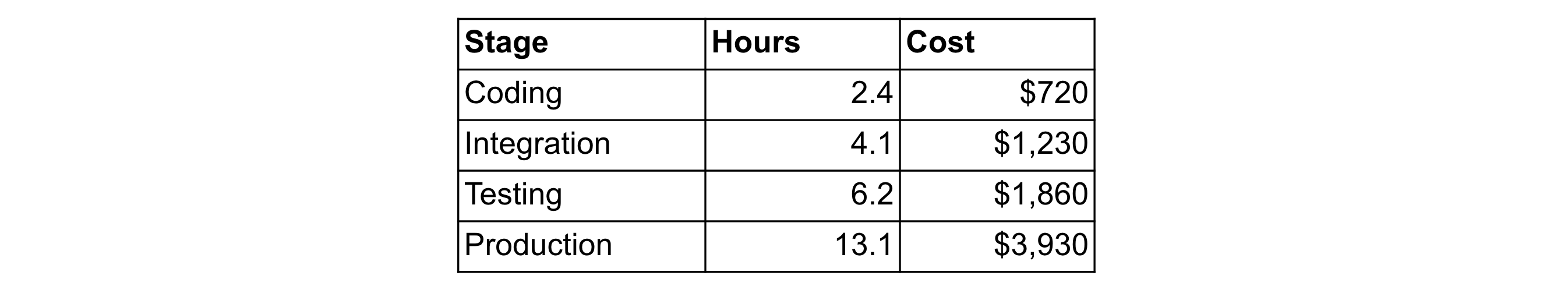
These costs are just the start of the financial impact when the software bug is also a software vulnerability. IBM, in partnership with the Ponemon Institute, put the average cost to remediate a data breach in 2020 at $3.86 million (USD). This does not take into consideration the reputation impact to the organization.
Having visibility into security risk in just development only provides you with half of the picture. Development and SecOps teams need to have a closed feedback loop enabling both teams to be successful. Development teams can gain insight into attacks targeting the applications they develop. This allows them to prioritize vulnerabilities correctly, enabling proactive resolutions to reduce risk. Likewise, SecOps teams can gain insight from their development counterparts, providing them with visibility into how the application works. This allows them to best apply proactive measures to mitigate attacks targeting the application until development can fix the vulnerability.
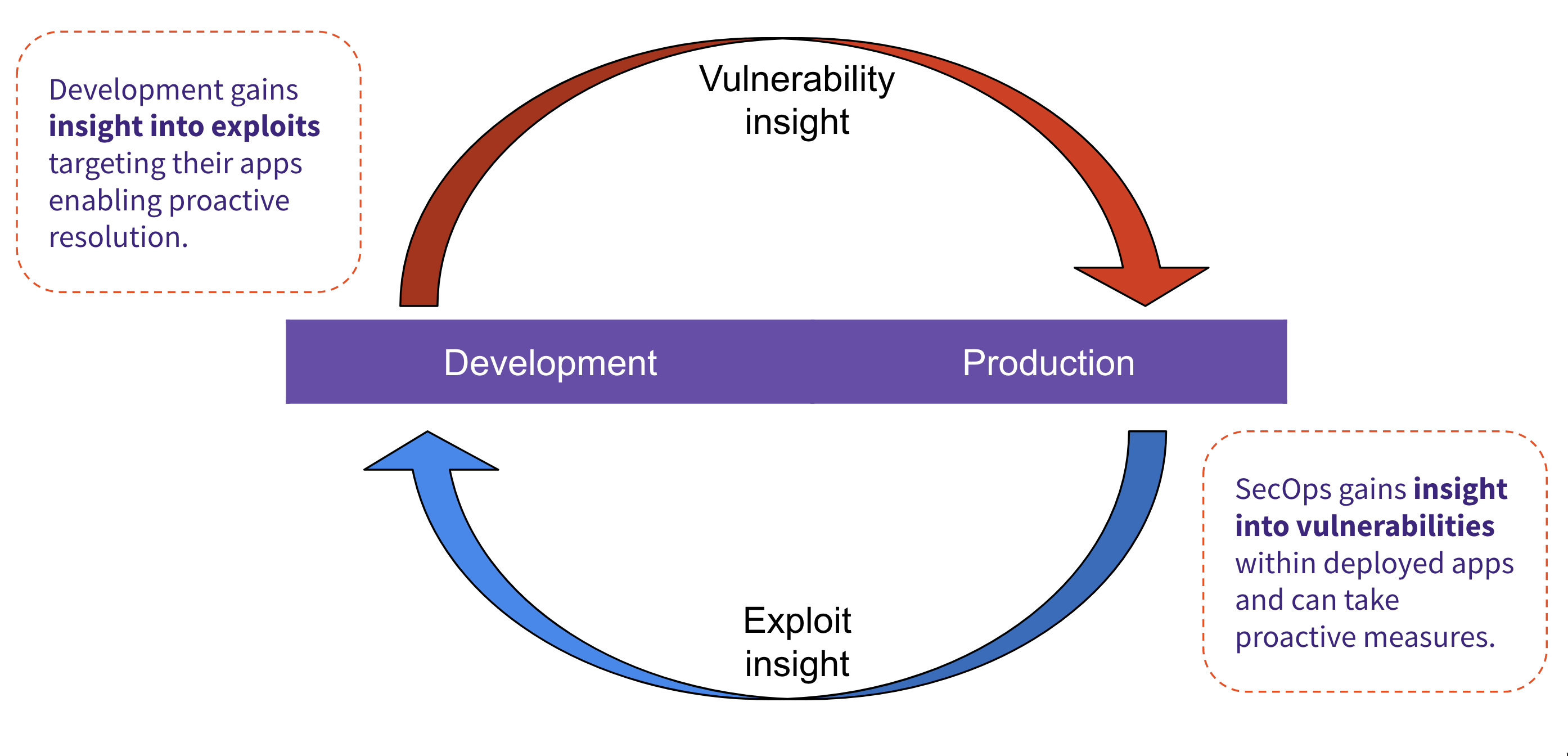
Closing the loop requires close collaboration, transparency, and efficiencies that only a single platform for the entire DevOps lifecycle can provide. Shifting security left while also providing protection for applications in production within a single application empowers teams to work closer together. Security is a team sport, and teams working together can best reduce their organization's overall security risk.
The Sec section is made up of three stages of the DevSecOps lifecycle, along with the groups in those stages:
Team members for the Sec Section can be found in the links below:
Team members can learn more about GitLab's investment into the Sec section by checking the Product Investment page in the internal handbook.
A complete list of released features can be found in the Release Feature Overview.
The increasing pace of modern software development demands that we push security testing further left than before, integrating it into existing workflows rather than forcing teams to adapt their processes or context-switch to separate tools.
Moving security scanning directly into the IDE and pre-commit stages enables developers to catch vulnerabilities, exposed secrets, and dependency issues before they even enter the codebase, dramatically reducing remediation costs and team overhead.
For this proactive approach to succeed, security tools must provide clear, actionable feedback that developers can understand without deep security expertise, including precise code locations and step-by-step remediation guidance with examples of secure coding patterns.
By making security both approachable and efficient, we help organizations build a true DevSecOps culture where security becomes a natural part of every developer's daily work, transforming how organizations approach application security while significantly reducing the burden on overburdened security specialists.
To achieve this theme, GitLab will pursue capabilities like:
In today's complex security landscape, presenting raw vulnerability data without context can lead teams to work on less impactful tasks or accept risks without realizing the consequences. That doesn't work well for anyone.
By combining multiple security scanning methods and leveraging more advanced techniques like AI and machine learning, we can provide deeper context and more accurate risk assessments for each security finding. This intelligence-driven approach helps teams cut through the noise of security alerts, focusing remediation efforts on vulnerabilities that pose the greatest actual risk to their applications. Integration across different security disciplines creates a comprehensive view of each vulnerability's impact and exploitability, enabling more confident decision-making about when and how to remediate issues.
The power of machine learning transforms security scanning from a simple detection tool into an intelligent advisory system that helps teams make informed, strategic decisions about their security posture and resource allocation.
To achieve this theme, GitLab will pursue capabilities like:
When tools identify vulnerabilities but don't provide a clear path to resolution, organizations end up exposed to security risks for longer than necessary. Worse still, as backlogs of security issues grow, organizations end up accepting risks without realizing it—an untriaged and unresolved vulnerability is one that's tacitly accepted.
Modern security tools must go beyond detection to provide automated remediation pathways that help both developers and security teams efficiently address vulnerabilities.
As applications and security threats grow more complex, effective security programs have to rely on automation to scale up. By transforming security findings into automated actions, intelligent tools help organizations dramatically reduce their mean time to remediation while allowing both development and security teams to focus on strategic work rather than routine maintenance.
To achieve this theme, GitLab will pursue capabilities like:
Security teams need centralized management for their security and compliance workflows. Features such as user management, compliance labels, security policies, and the vulnerability and dependency lists need to allow for centralized management that applies across all of an organization's projects.
SSCS capabilities will ensure that compliance regulations are strictly followed in a way that they cannot be bypassed without the proper approvals. This includes providing the necessary tools to audit, monitor, and manage the compliance controls that are enforced.
SSCS capabilities will serve as a connection point for a seamless workflow spanning across the DevSecOps lifecycle. By enabling collaboration between types of users, SSCS can help solidify the advantages GitLab has to offer as a single application. For example, these areas might include the following:
SSCS capabilities will be pre-configured with reasonable defaults out-of-the-box whenever possible. When not possible, they will be easy to configure either through code or through a guided UI workflow that is friendly to users without coding knowledge. Regardless of how the capabilities are configured, they will be stored as code for ease of management.
For example, GitLab's security policy editor supports editing policies in both a rule mode and in yaml mode.
SSCS capabilities allow organizations to lock down every aspect of their supply chain. This includes securely authenticating users into GitLab, hardening the GitLab platform itself, and verifying every step along the DevSecOps lifecycle as code is created, built, and deployed.
The Sec section is composed of two stages, Secure and Govern, each of which contains several categories. Each stage has an overall strategy statement below, aligned to the themes for Sec. Each category within each stage has a dedicated direction page plus optional documentation, marketing pages, and other materials linked below.
The Application Security Testing (AST) stage helps customers find vulnerabilities in applications before they reach production. We focus on developing scanning capabilities to find these vulnerabilities, then we work closely with the Security Risk Management and Software Supply Chain Security stages to ensure that organizations can take action on the vulnerabilities our scanners detect.
GitLab was named as a Challenger in the 2022 Magic Quadrant for Application Security Testing.
Scans your application source code and binaries to spot potential vulnerabilities before deployment. SAST supports scanning a variety of different programming languages and automatically chooses the right analyzer even if your project uses more than one language. Vulnerabilities, additional data, and solutions are shown in-line with every merge request. Scanner results are collected and presented as a single report. This category is at the "complete" level of maturity.
Priority: high • Documentation • Direction
Scans your repository to help prevent your secrets from being exposed. Secret Detection scanning works on all text files, regardless of the language or framework used. Code pushed to a remote Git branch can be rejected if a secret is detected. This category is at the "viable" level of maturity.
Priority: medium • Documentation • Direction
Analyzes your source code quality and complexity. This helps keep your project’s code simple, readable, and easier to maintain. This category is at the "minimal" level of maturity.
Runs automated penetration tests to find vulnerabilities in web applications and APIs as they are running. DAST can run live attacks against a Review App, an externally deployed application, or an active API. Scans can be run for every merge request, on a schedule, or even on-demand. DAST supports user inputted HTTP credentials to test private areas of your application. Vulnerabilities, additional data, and solutions are shown in-line with every merge request. Scanner results are presented as a single report. This category is at the "complete" level of maturity.
Priority: high • Documentation • Direction
Secures and protects web Application Programming Interfaces from unauthorized access, misuse, and attacks. Tests for known vulnerabilities by performing penetration testing of APIs with DAST. Finds unknown vulnerabilities by performing Fuzz Testing of web API operation parameters.Users can provide credentials to test authenticated APIs. Vulnerabilities, additional data, and solutions are shown in-line with every merge request.. Scanner results are collected and presented as a single report. This category is at the "complete" level of maturity.
Priority: high • Documentation • Direction
Sends random inputs to an instrumented version of your application in an effort to cause unexpected behavior in order to identify a bug that needs to be addressed. Helps you discover bugs and potential security issues that other QA processes may miss. This category is at the "complete" level of maturity.
Priority: high • Documentation • Direction
Analyzes external dependencies within your application for known vulnerabilities on each CI/CD code commit. Vulnerabilities, additional data, and solutions are shown in-line with every merge request. Scanner results are collected and presented as a single report. Upon code commit, project dependencies are searched for approved and denied licenses defined by per project custom policies. Software licenses are identified if they are not within policy and are shown in-line for every merge request for immediate resolution. This category is at the "viable" level of maturity.
Priority: high • Documentation • Direction
Scans your container images for known vulnerabilities within the application environment. Image contents are analyzed against public vulnerability databases.Security findings, additional data, and solutions reported in-line with every merge request along with additional data including solutions. Results are presented as a single report. Container Scanning is considered part of Software Composition Analysis. This category is at the "viable" level of maturity.
Priority: medium • Documentation • Direction
The GitLab Advisory Database serves as a repository for security advisories related to software dependencies. GitLab integrates the advisory database with its proprietary and open-source application security scanning tools. In order to maintain the efficacy of those scanners, we strive to keep their underlying vulnerability databases up-to-date.
Priority: high • Direction
Continuously assess your applications and services are not vulnerable to security threats through automated, real-world emulated scenarios to identify weaknesses in your attack surface
Priority: low
Application Security Testing pricing and tiering reflects GitLab's overall pricing model.
We focus our efforts primarily on Ultimate. Advanced security is an Ultimate pricing theme and helps customers deliver on organization-wide security and compliance priorities.
Advanced features, including technology developed in-house at GitLab and technology we've acquired, are available only in Ultimate.
We make a subset of our AST scanners available in all tiers (including Free). We typically do this when the scanners are themselves open-source.
We do not specifically focus on Premium.
The Software Supply Chain Security (SSCS) stage helps organizations to reduce their overall risk by applying appropriate management and governance oversight across the entire DevSecOps lifecycle. SSCS provides management tools to secure the GitLab platform itself by restricting access to authenticated users and ensuring they are provisioned with the least amount of required privileges. To help manage and monitor risk levels, the SSCS stage provides visibility into user permissions and activity; project dependencies; security findings; and adherence to compliance standards. This visibility is then coupled with enforcement capabilities to proactively prevent risks by automating compliance and securing the software supply chain.
System Access provides tools to authenticate through all points of GitLab (UI, CLI, API). These tools allow you to configure what an individual/process has access to once they authenticate, determined by their role. GitLab integrates with several OmniAuth providers, LDAP, SAML, and more.
GitLab provides various permissions and roles in order to evaluate what access or rights an identity should have in an environment. Custom roles can also be created to allow an organization to create user roles with the precise privileges and permissions desired.
Audit Events track important actions within GitLab along with who performed the actions and the time in which they occurred. These events can be used in a security audit to assess risk, strengthen security measures, respond to incidents, and adhere to compliance. This category is at the "viable" level of maturity.
Priority: high • Documentation • Direction
Compliance Management provides customers with the tools necessary to ensure and manage their compliance programs. Compliance Workflow Automation is provided to enforce custom pipelines to run on projects which have specific compliance needs. For compliance oversight, the Compliance Center provides a central location for compliance teams to manage their compliance standards adherence reporting, violations reporting, and compliance frameworks for their group. This category is at the "viable" level of maturity.
Priority: high • Documentation • Direction
Dependency Management allows users to review project/group dependencies and key details about those dependencies, including their vulnerabilities, licenses, and packager. This category is at the "viable" level of maturity.
Priority: high • Documentation • Direction
GitLab allows you to secure your software supply chain including push rules, code scanning, SBOM management, and enforcement of compliance policies. This category is at the "viable" level of maturity.
Priority: high • Learn more • Documentation • Direction
Insider Threat identifies attacks and high risk behaviors by correlating different data sources and observing user behavioral patterns
Instance Resiliency provides tools to prevent malicious activity from occurring within GitLab Instances. These tools include external pipeline validation allowing you to use an external service to validate a pipeline before it is created.
Secure and protect access to secrets, such as API keys and passwords, to ensure that sensitive data is protected throughout your development process. This category is at the "viable" level of maturity.
Artifact Security focuses on the hardening of artifacts, to ensure the authenticity of artifacts.
Release Evidence provides assurances and evidence collection that are necessary for you to trust the changes you're delivering. When a release is created, GitLab takes a snapshot of relevant release data as evidence that it occurred. This category is at the "viable" level of maturity.
SSCS is focused on providing governance and compliance features that span across the DevSecOps lifecycle. SSCS's tiering strategy aligns with the GitLab approach of selecting the tier based on who cares most about the feature. Because Executives generally care most about governance features, it is expected that most SSCS features will land in the Ultimate tier.
This tier is the primary way to increase broad adoption of the SSCS stage, as well as encouraging community contributions and improving security across the entire GitLab user base.
As a general rule of thumb, features will fall in the Free tier when they meet one or more of the following criteria:
This tier is not a significant part of SSCS's pricing strategy; however, a few features features that primarily appeal to Directors rather than Executives may fall into the Premium tier. One example of this is our audit event functionality that is available in this tier.
This tier is the primary focus for the SSCS stage as most SSCS features enable executives to ensure that their organization meets compliance requirements and maintains an acceptable security posture.
As a general rule of thumb, features will fall in the Ultimate tier when they meet one or more of the following criteria:
Last Updated: 2025-02-20