Maintenance Mode
Maintenance Mode
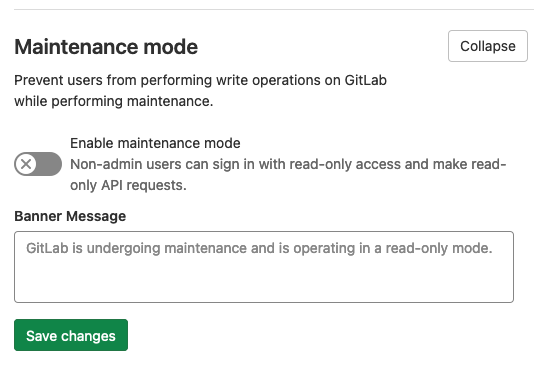
Systems administrators occasionally perform maintenance operations on their GitLab instance to keep it performing optimally. Administrators want to offer the highest level of access to their users while these operations are taking place. For example, you may want to perform a failover test to a secondary site as part of the company’s business continuity plan. Prior to the failover, you want to pause changes for a short period to ensure the secondary is fully synchronized. Until GitLab 13.8, you could restrict users from logging in, but this would block the entire UI and would render GitLab inaccessible to users.
GitLab 13.9 introduces maintenance mode, where write operations are disabled at the application level. This means that GitLab is effectively in a read-only state for all non-administrative users (administrators are still able to edit application settings and background jobs continue). Regular users are able to log in to GitLab, view the interface and perform other read-only operations, such as git clone or git pull. Using maintenance mode, systems administrators can perform maintenance operations, such as failing over to a secondary site, with minimal disruption to regular users.
Note that GitLab already supports zero-downtime updates and enabling maintenance mode is not required to keep your instance up-to-date.
Release Analytics at the group level
Release Analytics at the group level
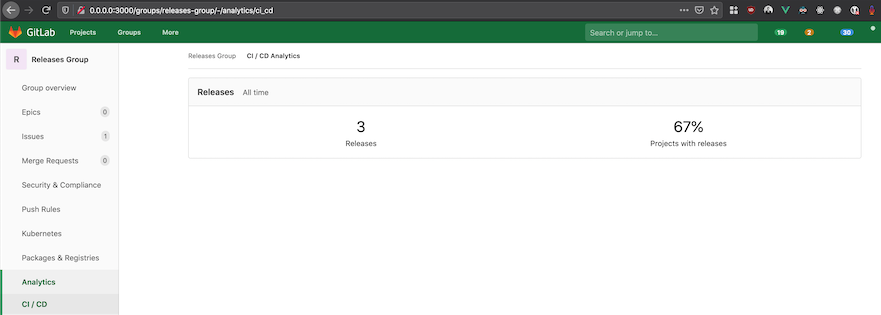
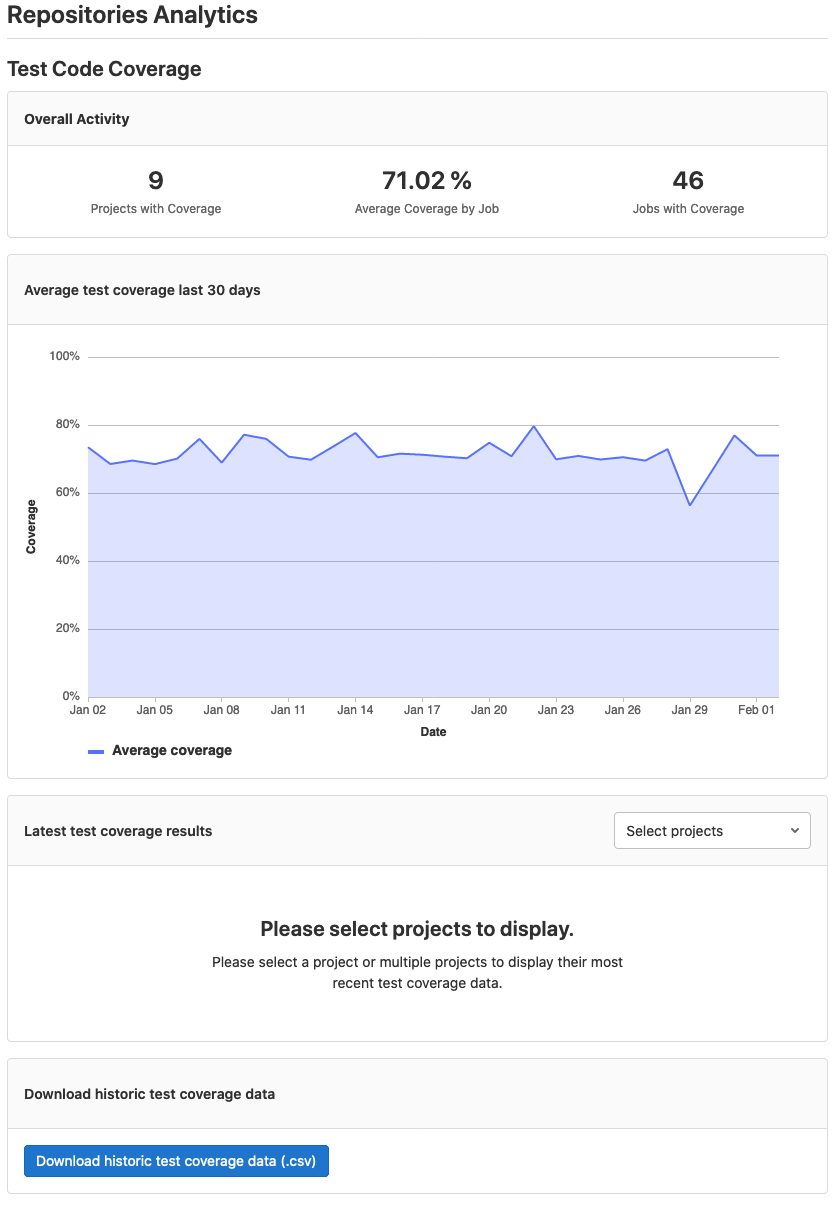
In GitLab 13.9, you can view group-level release analytics. This provides you with an aggregated view of all release metrics for each of the projects associated to that group. You can view how many releases belong to this group and what percent of the projects are associated with releases. This feature also serves as a first iteration towards supporting DORA 4 metrics at the group level.
JavaScript and Python support for coverage-guided fuzz testing
JavaScript and Python support for coverage-guided fuzz testing
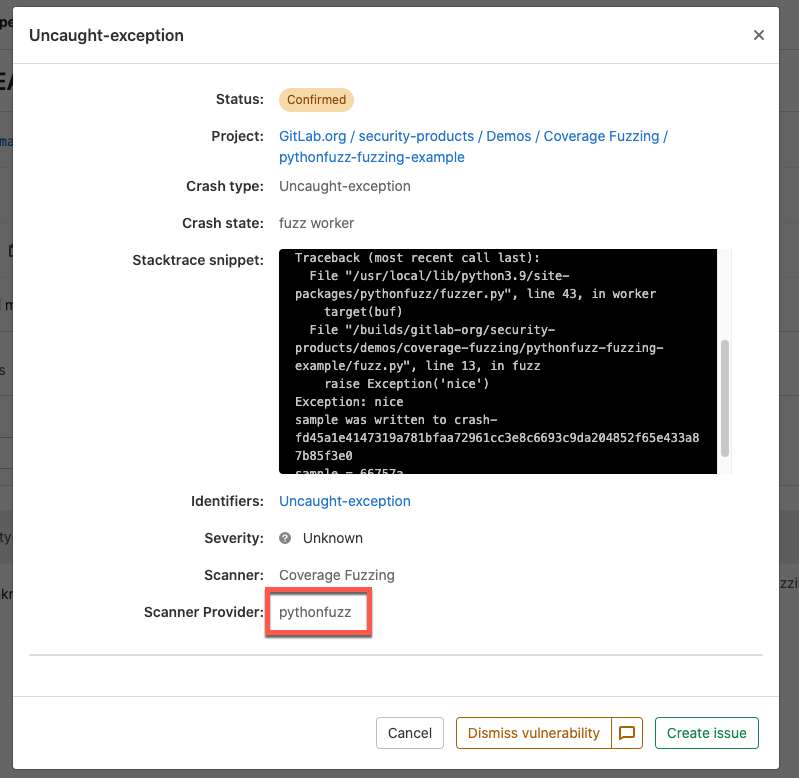
You can now run coverage-guided fuzz tests against your Python and JavaScript apps! These are two of the most popular languages and we’re excited to support them for use in coverage-guided fuzz testing.
To run fuzz tests against apps written in these languages, use the same workflow you would for any other supported language. Create a fuzz testing job to run in your pipeline. When GitLab runs it, any fuzzing results automatically appear in the Security Dashboard, and in the Security tab of the pipeline.
Override Gitaly Cluster replication factor for specific repositories
Override Gitaly Cluster replication factor for specific repositories
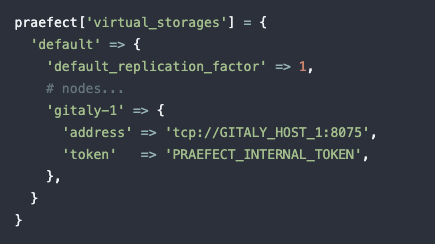
Previously, the replication factor of a Gitaly Cluster was the number of nodes in the cluster. This made it impossible to enable Gitaly Cluster for GitLab instances with very large storage requirements. For example, a 500 TB cluster with 50 nodes would require 25 PB of storage space to be provisioned. To enable Gitaly Cluster to be used for instances with large storage requirements, a way was needed to specify a replication factor less than the total number of nodes in the cluster.
In GitLab 13.9, the replication factor for each repository can be set individually to any number less than the number of nodes in the cluster. This allows for replication of only the most important or active repositories, leaving other less critical repositories on a smaller number of nodes. This will allow organizations to tune their clusters to their own storage and budget constraints. We have also enabled a method to configure a default replication factor for all newly created repositories. This should provide users the necessary means to horizontally scale their Gitaly Cluster.
Easily see repeat failed tests in Unit Test Reports
Easily see repeat failed tests in Unit Test Reports
When you are reviewing failed tests in a pipeline, it’s difficult to tell if a failing test is a legitimate failure that needs investigation or a flaky test that will pass on the next execution.
The next iteration of the repeat failed test counter adds the repeat failed test counter to the unit test report. Now you can see how often a test has failed on the default branch without needing a merge request associated with the test execution.
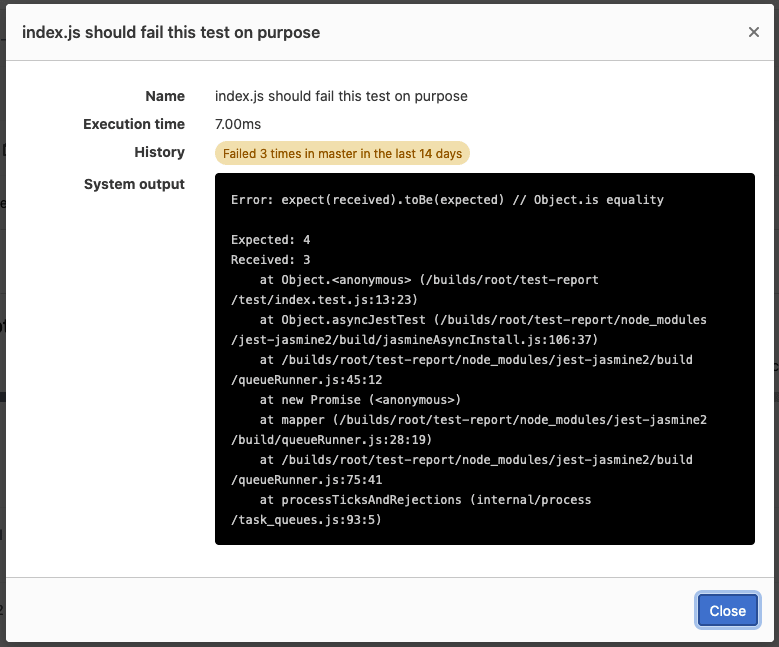
Select CI/CD configuration from any job and reuse it
Select CI/CD configuration from any job and reuse it
Previously, if you wanted to reuse the same configuration in multiple jobs, you had two options: add YAML anchors, which don’t work across different configuration files, or use extends to reuse an entire section.
In this release, we’ve added a new YAML function called !reference, which lets you target the exact configuration you want to reuse as part of your CI/CD pipeline, even if it’s in another file.
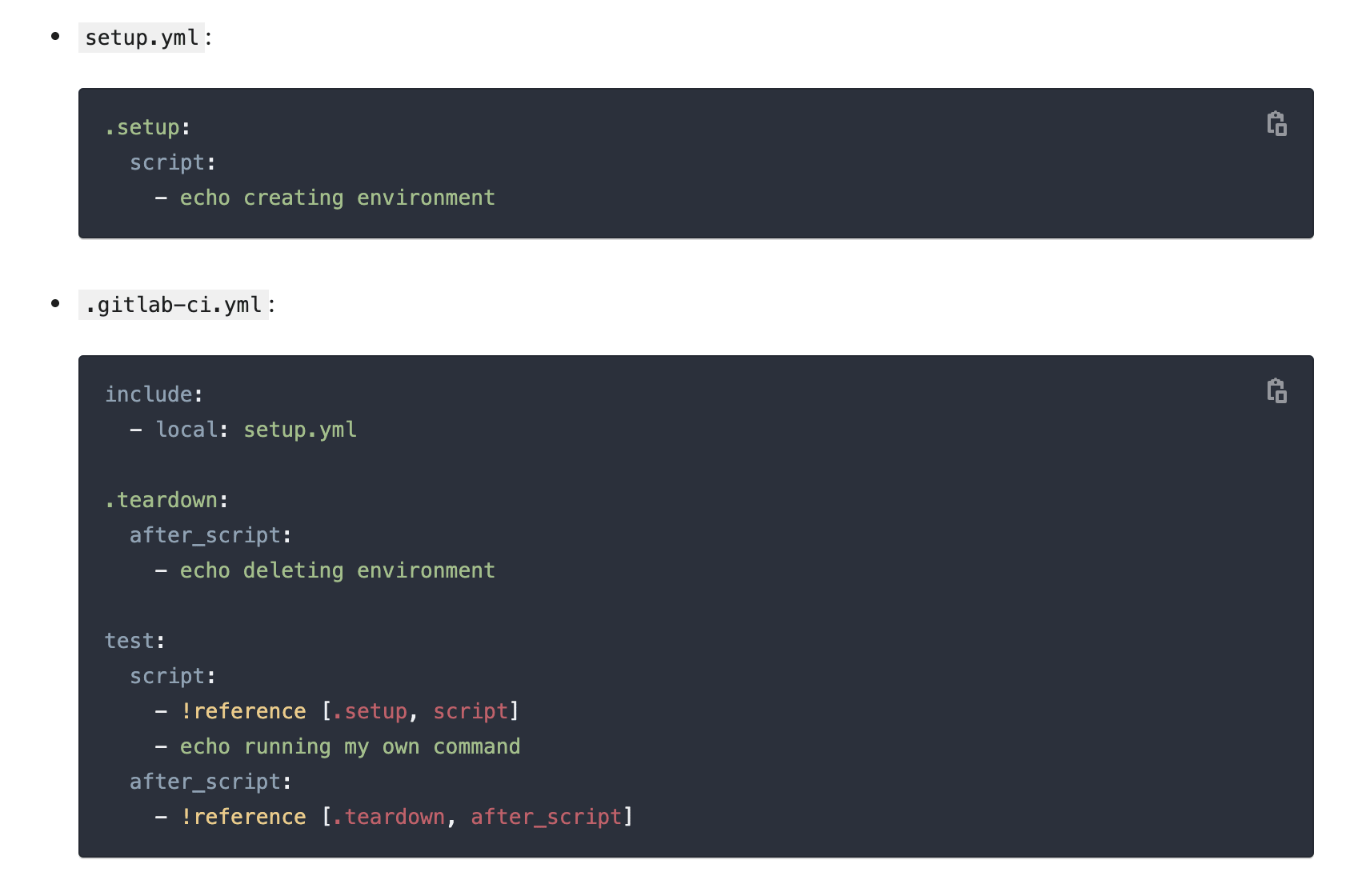
View an expanded version of the CI/CD configuration
View an expanded version of the CI/CD configuration
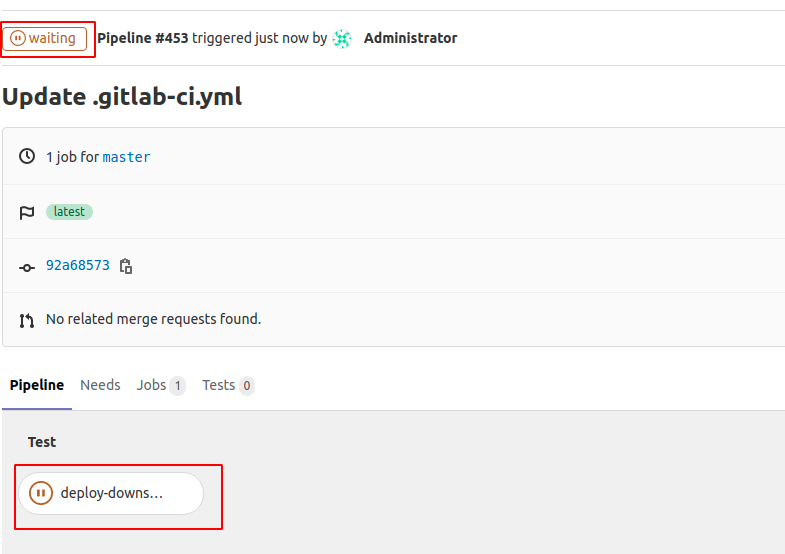
When configuring pipelines, you use keywords like include and extends often. These keywords help break down one long pipeline configuration file into multiple files, which increases readability and reduces duplication. Unfortunately, those keywords can make a pipeline configuration hard to follow. In some configurations, a pipeline configuration file can be mostly composed of a list of other included configuration files.
In this release, you can view a version of your pipeline configuration with all of the include and extends configurations merged together. It’s now much easier to understand more complex pipeline flows and simplifies the debugging process.
Resource Group for multi-project and parent-child pipelines
Resource Group for multi-project and parent-child pipelines
You can now benefit from using resource groups if your deployment process uses child pipelines or multi-project pipelines. Such pipelines may contain multiple stages, multiple jobs, and even span across multiple projects. Resource groups ensure only one downstream deployment pipeline runs at a time so you can deploy safely. Previously, resource_group only supported deployment jobs in the same project.
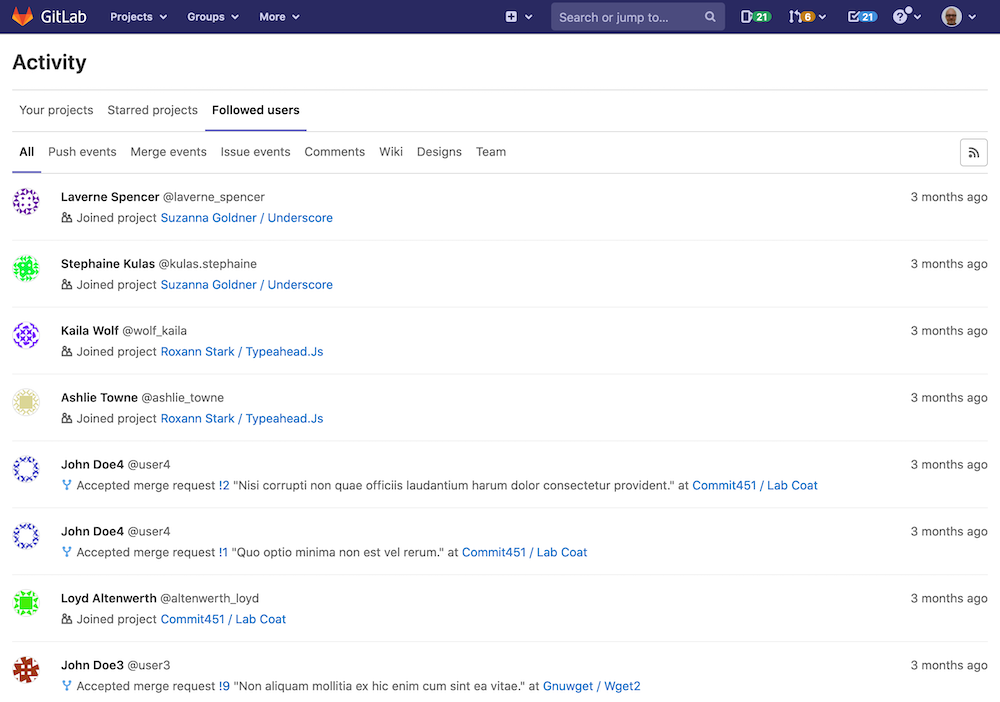
Follow user activity
Follow user activity
GitLab users can now follow other users’ activity in GitLab! Following users helps you to stay updated on activity by team mates and key project contributors. You can follow or unfollow other users from their user profiles. To see their activity go to the top-level Activity view, and select the Followed Users tab.
Thanks to the amazing work from GitLab contributor Roger Meier from Siemens over the past 3 months, this feature is now available in 13.9.
Create Jira issues from Vulnerabilities
Create Jira issues from Vulnerabilities
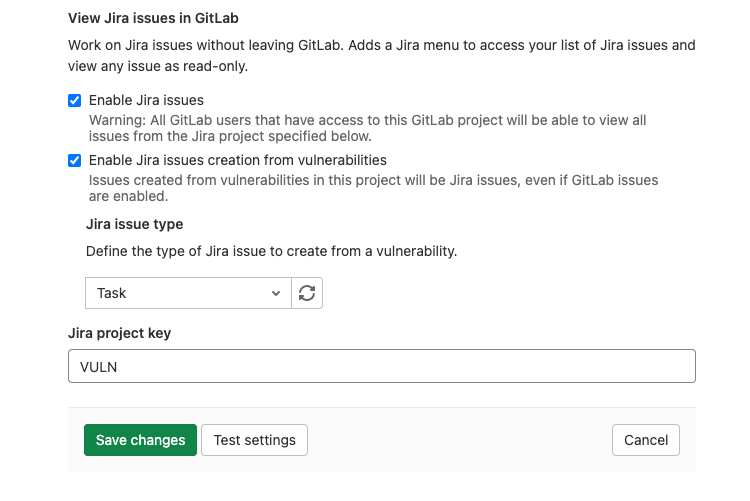
Many customers use Jira as their single source of truth for tracking issues and engineering work. When using GitLab for SCM and CI/CD, they can take advantage of our existing integration to pass information from MRs and commits into existing Jira issues. However, until now there has been no way to automatically pass information about vulnerabilities detected by security scanners into Jira. This leaves users who rely on Jira to track work no choice but to manually copy vulnerability information into new Jira issues.
To address this, we’re introducing a new ability to create Jira issues directly from a vulnerability’s details. You will see this as a new option in your existing Jira integration settings. Simply enable the new option and select the desired Jira issue type. Available issue types are pulled automatically based on the currently configured Jira target project. Once enabled, all places in your project where you can create GitLab issues from a vulnerability will instead directly create a Jira issue of the configured type.
Markdown links for Feature Flags
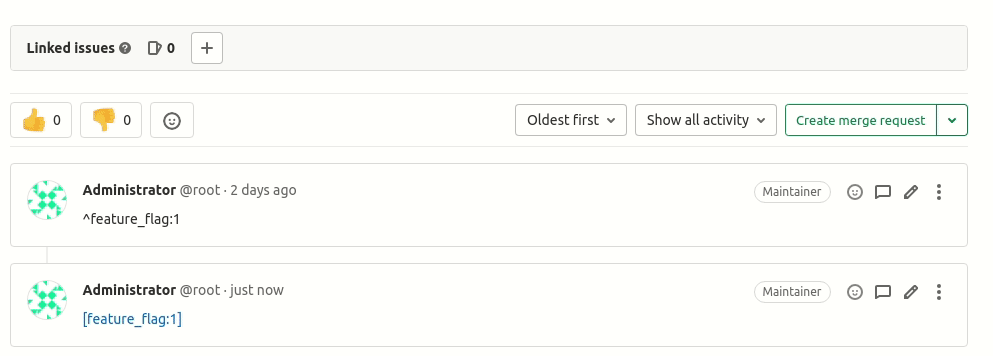
Markdown links for Feature Flags
This release adds Markdown linking for Feature Flags. Users can mention [feature_flag:<IID>] in discussions or comments to refer a specific Feature Flag. Click on the generated link to go to that Feature Flag’s edit page. This makes collaboration on Feature Flags much easier and more convenient.
Allow Deploy Keys to push to protected branches
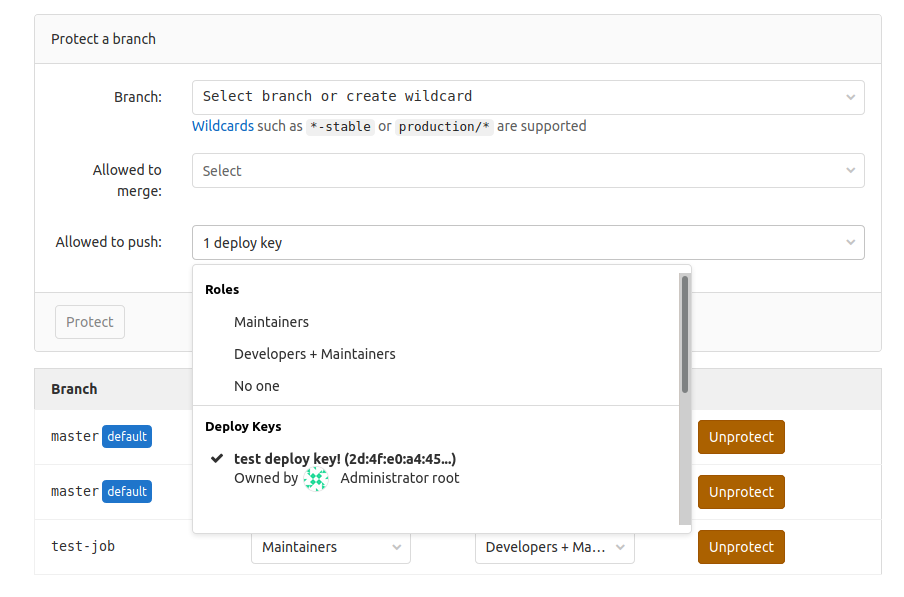
Allow Deploy Keys to push to protected branches
Prior to GitLab 12.0, Deploy Keys with write access could push commits to protected branches. Support for this was removed due to security concerns, but many users still requested it, as they were using it to ensure that only users with Deploy Keys could push to their repositories. It also eliminates the need to use a service user or machine user, which ties up a license for any team that wants to allow Deploy Keys to push to protected branches just for this use case. We are excited to announce that we resolved this issue and now Deploy Keys can push to protected branches once more while abiding by security best practices. By moving towards an isolated permission model for Deploy Keys, users can now select Deploy Keys to link to protected branches directly from the settings page on protected branches.
Request a follow-up review from a Reviewer
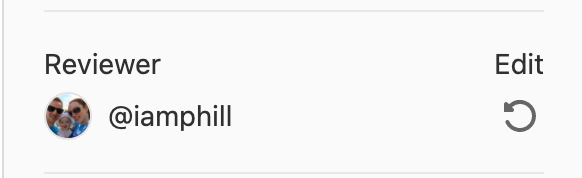
Request a follow-up review from a Reviewer
Merge request authors receive feedback from reviewers. Often, this feedback needs to be re-reviewed to make sure all issues have been appropriately addressed. As the author of the contribution, you need to communicate the need for a follow-up to your reviewer.
For reviewers who have already reviewed a merge request, you can now request a re-review. This request triggers a To-Do item and email notification to alert the user that you need a follow-up review of your contribution.
Improvements to the GitLab.com for Jira Cloud Application
Improvements to the GitLab.com for Jira Cloud Application
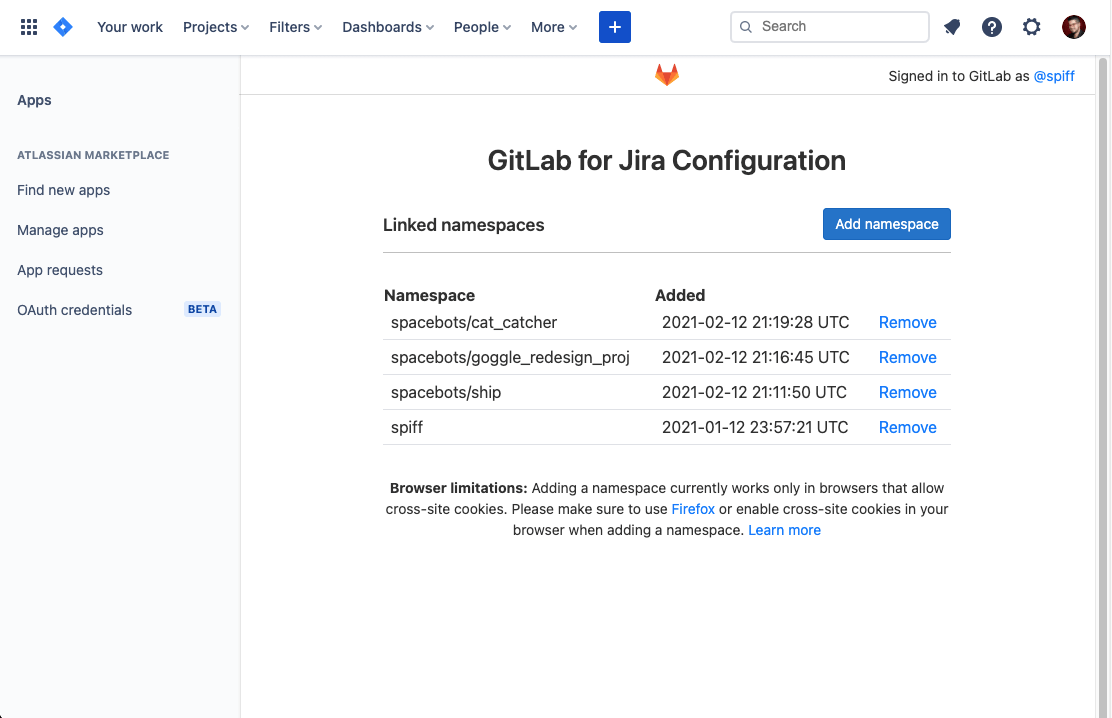
You can now sync your Jira Cloud project data with GitLab by using the GitLab.com for Jira Cloud application, available on the Atlassian Marketplace. This plugin displays information about your branches, commits, merge requests, deployments, and feature flags in the Jira Development Panel. Use it to see the current status of work in progress, then quickly navigate back to those pages inside of GitLab.
To make these features easier to use, we’ve made significant improvements to the initial setup process over the last few milestones, and now getting your GitLab namespaces connected is easier than ever. To get started, check it out on the Atlassian Marketplace.



We want to hear from you
Enjoyed reading this blog post or have questions or feedback? Share your thoughts by creating a new topic in the GitLab community forum.
Share your feedback