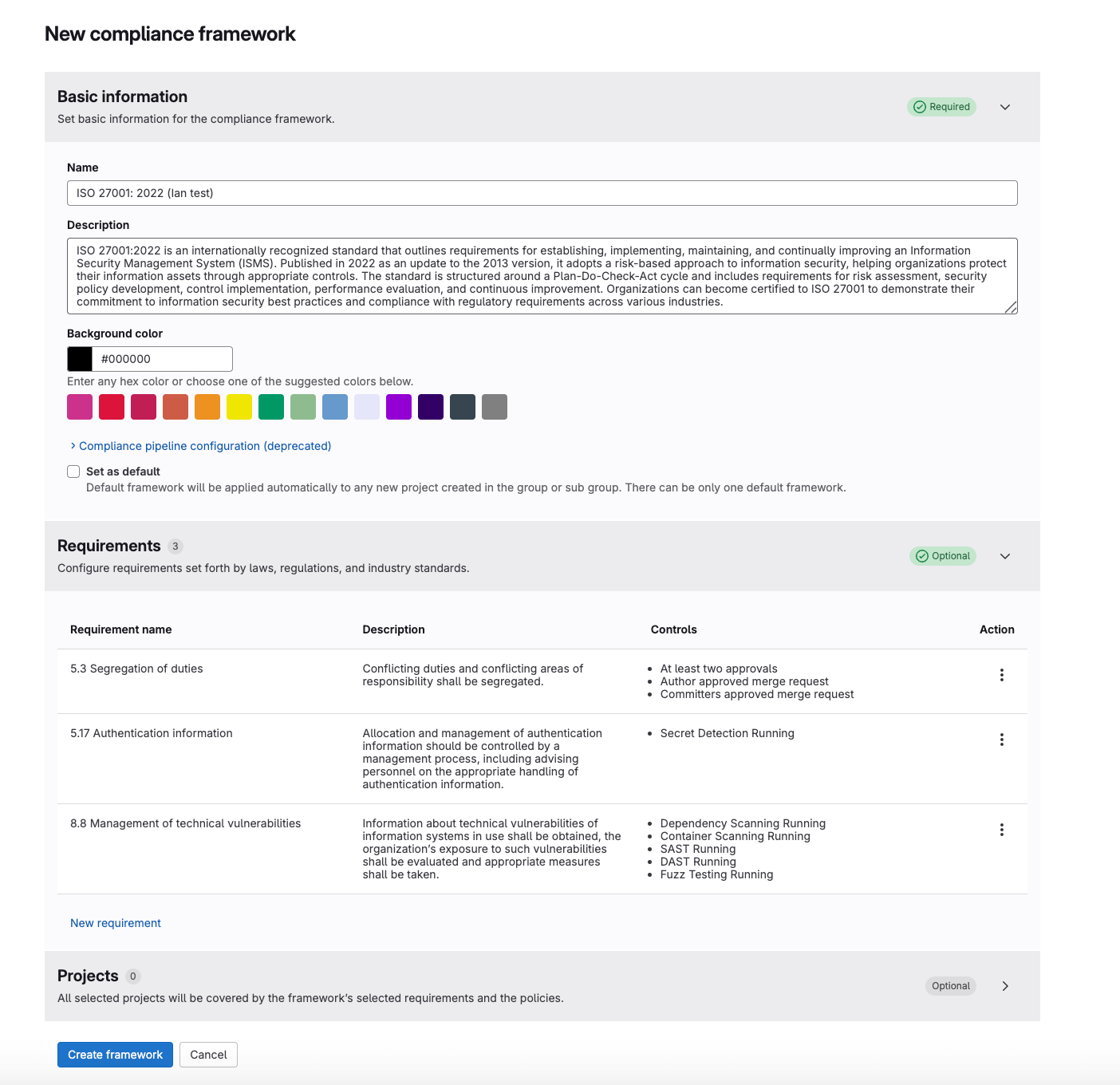
Customise compliance frameworks with requirements and compliance controls
Customise compliance frameworks with requirements and compliance controls
Previously, compliance frameworks in GitLab could be created as a label to identify that your project has certain compliance requirements or needs additional oversight. This label could then be used as a scoping mechanism to ensure that security policies could be enforced on all projects within a group.
In this release, we are introducing a new way for compliance managers to get more in-depth compliance monitoring in GitLab through ‘requirements’.
With requirements, as part of a custom compliance framework, you can define specific requirements from a number of different compliance standards, laws, and regulations that must be followed as an organization.
We are also expanding the number of compliance controls (previously known as compliance checks) that we offer from five to over 50! These 50 out-of-the-box (OOTB) controls can be mapped to the compliance framework requirements.
These controls check particular project, security, and merge request settings across your GitLab instance to help you meet requirements under a number of different compliance standards, laws, and regulations such as SOC2, NIST, ISO 27001, and the GitLab CIS Benchmark.
Adherence to these controls are reflected in standard adherence report, which is redesigned to take into account requirements and the mapping of controls to those requirements.
In addition to expanding our OOTB controls, we now allow users to map requirements to external controls, which can be for items, programs, or systems that exist outside the GitLab platform. These mappings allow you to use the GitLab compliance centre as the single source of truth when it comes to your compliance monitoring and audit evidence needs.
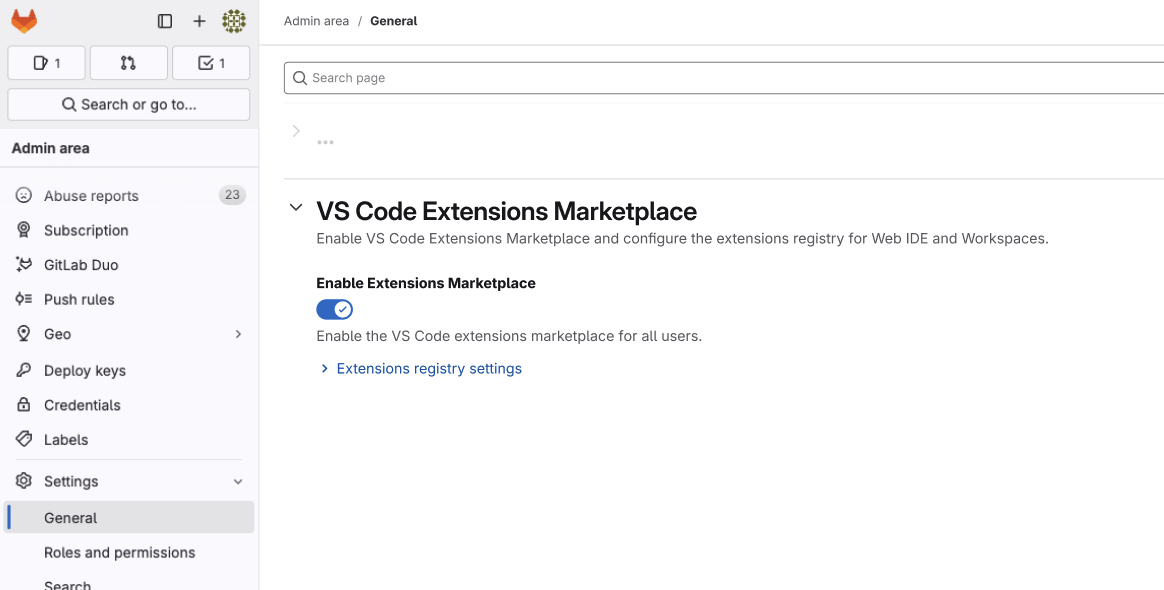
Extension marketplace for Web IDE on self-managed instances
Extension marketplace for Web IDE on self-managed instances
We’re thrilled to announce the launch of the extension marketplace in the Web IDE for self-managed users. With the extension marketplace, you can discover, install, and manage third-party extensions to enhance your development experience.
By default, the GitLab instance is configured to use the Open VSX extension registry. To activate this, follow the enable with default extension registry steps.
If you want to use your own or custom registry, you also have the option to connect a custom extension registry. This provides you with more flexibility to manage available extensions.
After enabling the extension marketplace, individual users must still opt in to use it. They can do this by going to the Integrations section in their Preferences settings.
It’s important to note that some extensions require a local runtime environment and are not compatible with the web-only version. Despite this, you can still choose from thousands of available extensions to boost your productivity and customize your workflow.
Enhance security with protected container tags
Enhance security with protected container tags
Container registries are critical infrastructure for modern DevSecOps teams. Until now, GitLab users with the Developer role or higher could push and delete any container tag in their projects, creating risks of accidental or unauthorized changes to production-critical container images.
With protected container tags, you now have fine-grained control over who can push or delete specific container tags. You can:
- Create up to five protection rules per project.
- Use RE2 regex patterns to protect tags like
latest, semantic versions (for example,v1.0.0), or stable release tags (for example,main-stable). - Restrict push and delete operations to Maintainer, Owner, or Administrator roles.
- Prevent protected tags from being removed by cleanup policies.
This feature requires the next-generation container registry, which is already enabled by default on GitLab.com. For GitLab Self-Managed instance, you’ll need to enable the metadata database to use protected container tags.
Safeguard your registry with protected Maven packages
Safeguard your registry with protected Maven packages
We’re thrilled to introduce support for protected Maven packages to enhance the security and stability of your GitLab package registry. Accidental modification of packages can disrupt the entire development process. With protected packages, you can safeguard your most important dependencies against unintended changes.
In GitLab 17.11, you can now protect Maven packages by creating protection rules. If a package matches a protection rule, only specified users can push new versions of the package. Package protection rules prevent accidental overwrites, improve compliance with regulatory requirements, and reduce the need for manual oversight.
Protected packages support for Maven and other package formats are all community contributions from gerardo-navarro and the Siemens crew. Thank you, Gerardo, and the rest of the crew from Siemens for their many contributions to GitLab! If you want to learn more about how Gerardo and the Siemens crew contributed this change, check out this video in which Gerardo shares his learnings and best practices for contributing to GitLab based on his experience as an external contributor.
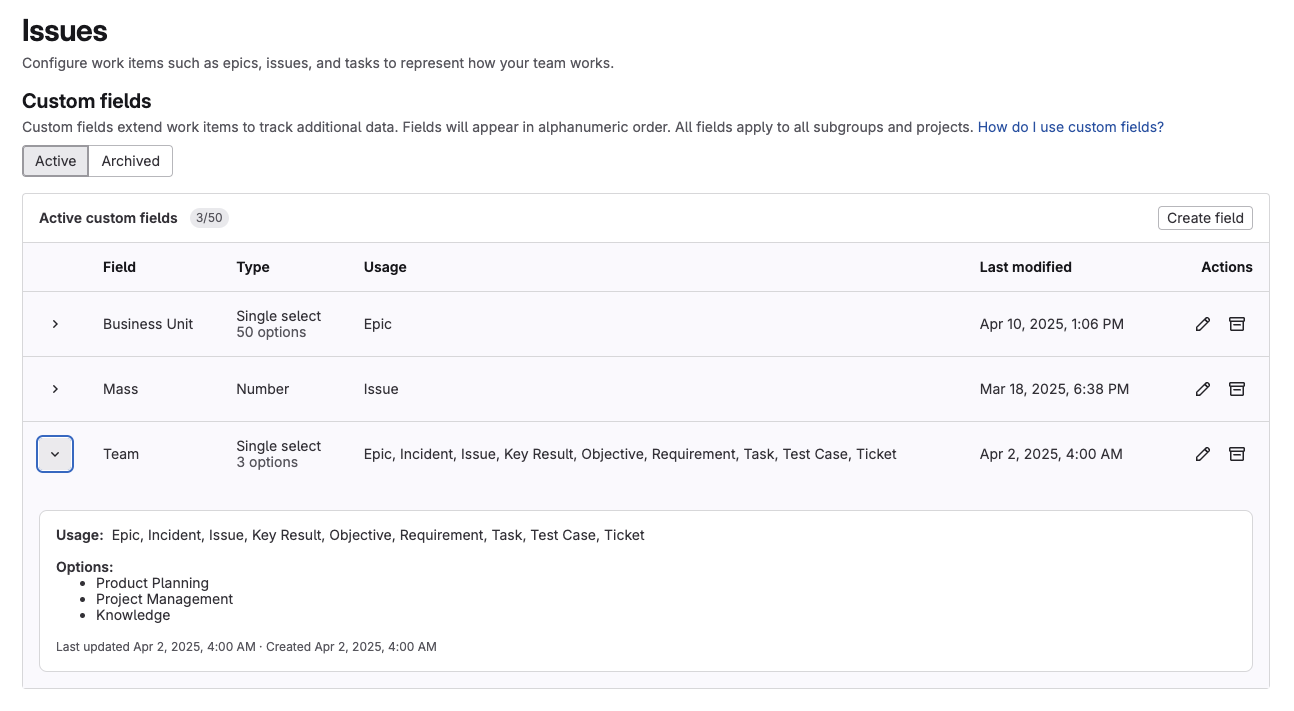
Epic, issue, and task custom fields
Epic, issue, and task custom fields
With this release, you can configure text, number, single-select, and multi-select custom fields for issues, epics, tasks, objectives, and key results. While labels have been the primary way to categorize work items up to this point, custom fields provide a more user-friendly approach for adding structured metadata to your planning artifacts.
Custom fields are configured in your top-level group and cascade to all subgroups and projects. You can map fields to one or more work item types and filter by custom field values in the issues and epics lists.
New issue look now generally available
New issue look now generally available
As of this release, the new issue look is generally available and replaces the legacy issue experience. Issues now share a common framework with epics and tasks, featuring real-time updates and workflow improvements:
- Drawer view: You can open items from lists or boards in a drawer for quick viewing without leaving your current context. A button at the top lets you expand to a full-page view.
- Change type: Convert types between epics, issues, and tasks using the “Change type” action (replaces “Promote to epic”)
- Start date: Issues now support start dates, aligning their functionality with epics and tasks.
- Ancestry: The complete hierarchy is above the title and the Parent field in the sidebar. To manage relationships, use the new quick action commands
/set_parent,/remove_parent,/add_child, and/remove_child. - Controls: All actions are now accessible from the top menu (vertical ellipsis), which remains visible in the sticky header when scrolling.
- Development: All development items (merge requests, branches, and feature flags) related to an issue or task are now consolidated in a single, convenient list.
- Layout: UI improvements create a more seamless experience between issues, epics, tasks, and merge requests, helping you navigate your workflow more efficiently.
- Linked items: Create relationships between tasks, issues, and epics with improved linking options. Drag and drop to change link types and toggle the visibility of labels and closed items.
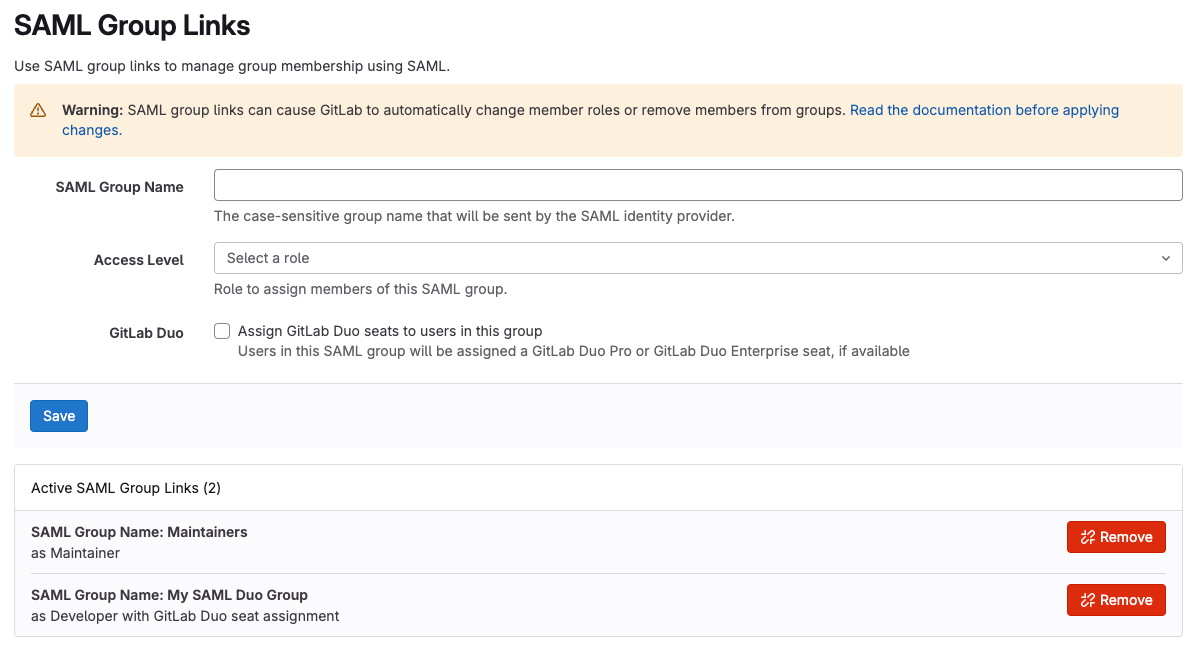
Automated Duo Pro and Duo Enterprise seat assignment
Automated Duo Pro and Duo Enterprise seat assignment
You can now automatically assign a Duo Pro or Duo Enterprise seat to users with SAML Group Sync. As long as the GitLab group has available Duo Pro or Duo Enterprise seats, any user mapped from the identity provider is automatically assigned a seat. This reduces the effort to manage seat assignments.